VPN Leak Test – Only 18 (Out of 105) VPNs Passed Our Audit [Weekly Updated]
Leveraging online privacy has become an impossible facet in recent times. Countries like the UK and Australia are pushing laws to impose mandatory data retention and engage in Mass Surveillance.
Governments under FVEY WANT TO SPY on their citizens, recording every digital interaction and activity. Then you have cases of cyberstalking, identity theft, and ransomware.
This all forces the hand of netizens to invest in a VPN solution, which provides anonymity by cloaking your IP address, hiding your browsing activities and interactions.
Encryption keeps your data anonymous from local ISPs, while allowing for the evading of geo-restriction and censored content. However, most VPNs are failing on their promises.
Most engage in logging session/connection data. Not to mention, “LEAKS” are becoming more common too, undermining the effectiveness of VPNs, exposing your true location and activities.
It is like buying a green vehicle only to have it blow smoke from the exhaust into the environment, which completely defies its purpose.
Hence, why BestVPN.co created this VPN Test guide, analyzing leak-related issues of over 100 different providers!
VPN Leak Test Report –
Explaining the Complexities of Different VPN Leaks
A dirty secret about the privacy tools industry: most VPNs leak! A detailed research piece from CSIRO found that 84% of free VPNs for Android leaked the users’ IP address.
Another study from the top10VPN.com, involving the testing of 150 free VPN apps with over 260M installs on Google Play, revealed 25% suffer with DNS leaks and 85% require shady PERMISSIONS.
I am always skeptical about providers that claim to be “free”. They cannot be trusted, as managing a VPN service does involve paying for dozens different facets.
Of course, there are plentiful paid counterparts that suffer from leakages too, and it is important that you avoid them. This is why I created this guide.
However, before I go into the details of those “broken” providers, it is important you understand different leaks for VPN security tests. So, let us get started with the basics:
WebRTC Leak
WebRTC is an open-source API definition that provides apps and browsers with RTC. It allows video and voice chats, along with P2P/File sharing within a browser, eliminating the need for plug-ins or extensions. It is the most commonly used API for browsers, like Mozilla and Firefox.
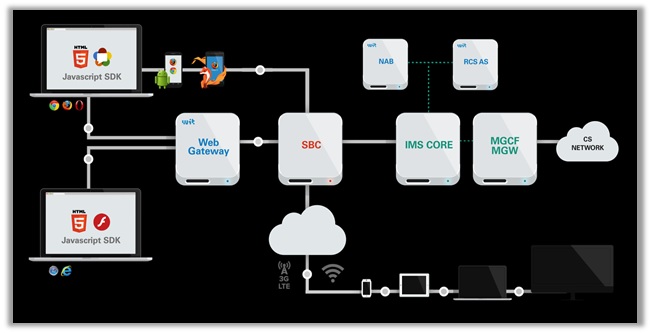
How Does a WebRTC Leak Occur?
To allow P2P functionality and video/voice chats, WebRTC uses a special mechanism. One that determines the public IP address, even if it is behind a NAT.
With a few JavaScript commands, WebRTC can send UDP packets to a Session Traversal Utilities (STUN) Server, which sends back a packet containing the IP address of who initiated the request.
This establishes special communication channels from the browser to the website. However, sometimes those channels may bypass the encrypted tunnel of VPNs, indicating a leak.
Such a leak will allow the website to access your true IP, while showing two public IP addresses to your ISPs, hence causing the website may block you and your ISP may end up reporting you.
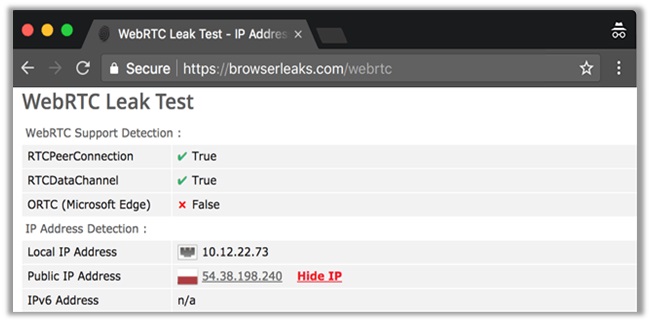
How to Receive Protection from WebRTC Leaks?
The STUN server receives requests outside the normal XMLHttpRequest. These are not visible in the developer console. As such, they cannot be blocked reliability even with plugins like WebRTC block.
The only way to receive protection from WebRTC leaks it use customized firewall rules. One that enforces traffic to only be sent via the encrypted VPN tunnel.
Most paid VPNs with established reputations will set this by default to prevent WebRTC leakage. However, to be sure you still need to perform a proper test VPN connection.
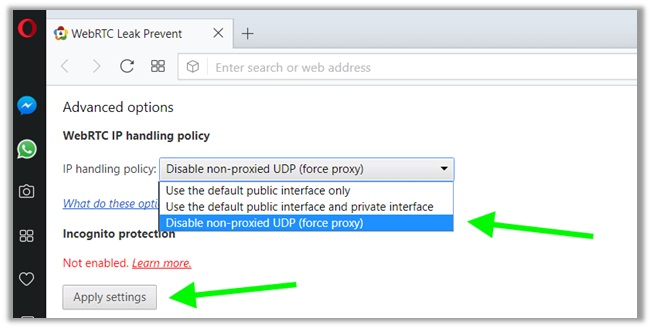
Another option is to use the WebRTC Leak Prevent extension available on the Chrome, Opera and Mozilla Stores, which further boosts your anonymity when using a VPN.
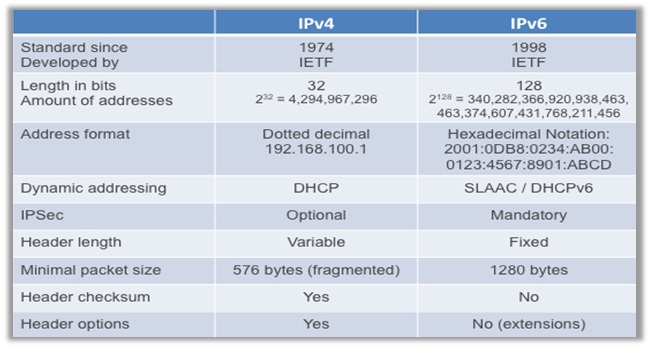
IP Address Leaks (IPv4 and IPv6)
IPv4 and IPv6 are both addresses that identify machines connected to a particular network. In principle, they are the same, but the way they function is different. IPv4 was the first version of IP, deployed in 1974 and still used till date. IPv6 came into being in the early 1994.
IPv4 is a connectionless protocol that requires less memory, offers video libraries/conferences, and already is supported by millions of devices. IPv6 is a good replacement for the former, adopting a hierarchical routing infrastructure, ideal for neighboring node interaction.
How Does an IPv4/IPv6 Leak Occur?
IPv4/IPv6 usually occur when there is a mismatch in the configuration between the operation system, your ISP, the VPN provider, and even individual devices.
If the configuration does not match, the leak can happen anytime. While most VPNs do not support IPv6, they still do happen to suffer with IPv4 leaks.
This can be quite dangerous, especially if you want to stay anonymous online. Only a total configuration in all fronts can prevent the IP address from leaking!
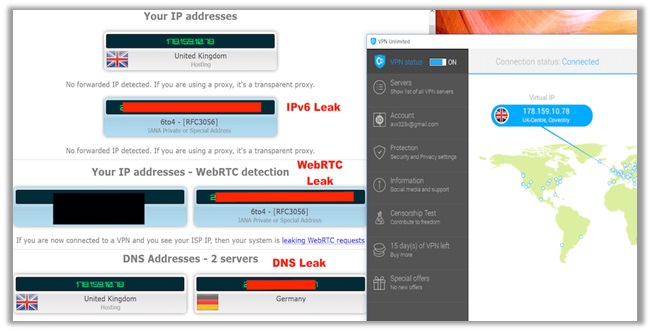
How to Receive Protection from IPv4/IPv6 Leaks?
Users can opt for a stronger tunneling protocol and encryption. Currently, the industry standard is military-grade AES-256-CBC ciphers on the OpenVPN (UDP and TCP protocols).

Another option is to manually create firewall rules that block all non-VPN traffic. IPv6 can also be used for better security, but the gradual transition from IPv4 is still due.
The simplest solution though is to get a VPN that does not leak IPv4 or IPv6 addresses. One that has been tested vigorously on multiple servers for confirmation about IP leak protection.
DNS Leaks
The Domain Name System (DNS) is a system that coverts domain names, like bestvpn.co, into a numerical IP address: 139.59.140.254 – which is more search-engine friendly. The translation process is handled by your ISP. However, since DNS requests are complete text logs of every website you visit, they can be quite problematic.
How Does a DNS Leak Occur?
A DNS leak occurs when translation requests are visible from the VPN tunnel, exposing the IP address and location of your ISP, along with your browsing history.
As such, when these DNS requests pass through your ISP, your identity becomes vulnerable. All your online activities become visible to your service provider.
If you are engaging in pirated streaming or torrenting, your ISP may report your illegal activities to copyright infringement hunters. This results in paying hefty DMCA fines!
As for the website you are visiting, if it is geo-restricted – you will be blocked from accessing the content and will get the “Streaming Error” or “content not available in your country” error.
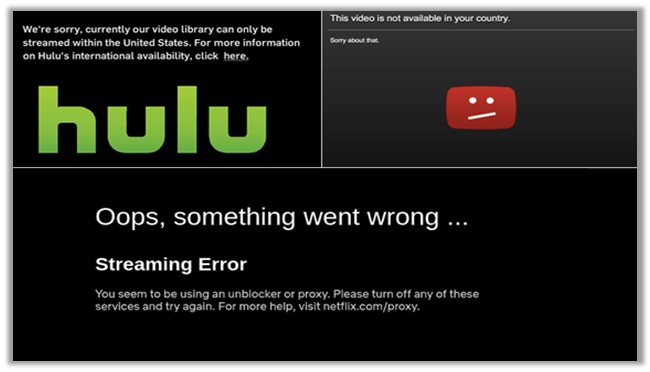
How to Test VPN and Receive Protection from DNS Leaks?
If you want to receive protection from DNS leaks, you will have to invest in a reliable provider. One that comes equipped with advanced features like WebRTC/DNS/IPv4 Leak Protection and internet kill switch.
The former activates a protocol for secure DNS, and the latter disables your internet connection upon the VPN client disconnecting, preventing your IP/DNS from leaking.
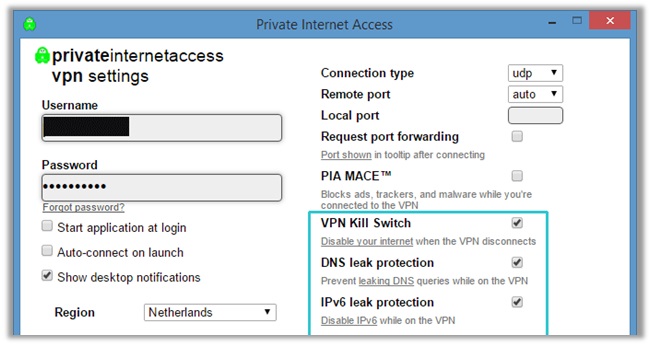
You can change your DNS address too for further protection. If you are using a VPN providers’ DNS server, they will provide you with alternative server addresses.
If you are using a public server, then a DNS server like the ones offered by Comodo Secure DNS, OpenDNS, and Google Public DNS should come in handy:
Comodo Secure DNS
- Preferred DNS server:26.56.26
- Alternate DNS server:20.247.20
OpenDNS
- Preferred DNS server:67.222.222
- Alternate DNS server:67.222.220
Google Public DNS
- Preferred DNS server:8.8.8
- Alternate DNS server:8.4.4
Testing 100+ Providers for IP/DNS/WebRTC Leaks
You probably have a good idea now how VPNs that leak could risk your online anonymity. The last thing you want to do is to sign up with a provider, suffering with WebRTC/DNS/IP leak issues.
In light of this, I conducted an in-depth analysis on over 100+ providers in the marketplace. I have created separate listings for VPNs that are secure (leak-free) and dangerous (no leak protection):
How Did I Perform Leak Tests on VPNs?
The VPN test process involved assessing providers for leakage indications. It included our own test VPN like checking for IP leaks through a missing or faulty kill switch, by deactivating and reactivating the network card.
Or like disconnecting the network connection for anywhere between 10 and 50 seconds to determine the IP directly after reconnection.
Apart from this, I also used various VPN test tools for calculating the exact risk associated to different products in the marketplace:
WebRTC and HTTP Request Leaks Tested Through:
DNS Leaks Tested Through:
IPv4/IPv6 and Torrent IP Leaks Tested Through:
I have used a combination of all these VPN tools to assess the accurate performance and security of a provider, but have only shown results from a select few of these services.
This was to save users the hassle of scrolling vigorously, as this Test My VPN guide is quite lengthy itself. Adding a lot of images also looks quite messy, compromising user-experience.
VPNs that Are Leak-Free – How to Test If Your VPN is Working!
- ExpressVPN
- NordVPN
- Surfshark
- VyprVPN
- Ivacy VPN
- StrongVPN
- IPVanish
- TunnelBear
- Windscribe
- PureVPN
- TorGuard
- CyberGhost
- IVPN
- Buffered
- ZenMate
- Mullvad
- GooseVPN
- Private Internet Access (PIA)
1) ExpressVPN
Server Used For VPN Test: Germany
The BVI-based provider tends to be an all-rounder, offering great privacy/security, streaming/torrenting capabilities, and an assortment of advanced features.
I tested the provider on several servers, including France, Australia, United Kingdom and Germany. The results you see below are for ExpressVPN’s Germany location from the IPLeak VPN test site.
Just to perform this testing in other ways, I have further tested ExpressVPN’s Germany server during its free trial period to assess its performance. And it turns out the ExpressVPN even on its free trial period doesn’t leak you IP address, hence you can count ExpressVPN as the top free VPN for Germany based on these IP leak test results.
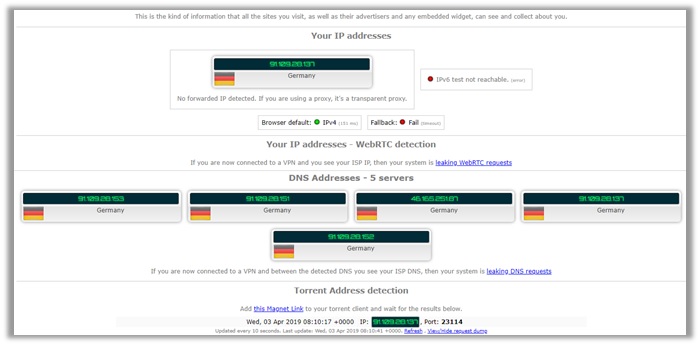
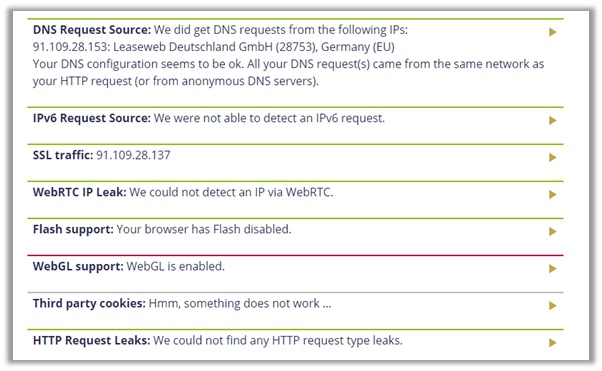
As you can see, the ExpressVPN DNS leak test, along with IPv4 address, WebRTC did not leak. Although, the Germany servers did display quite a few different DNS addresses.
It still did not reveal our true US location and the results remained consistent throughout tests conducted on IPLeak.net and doileak.com.
The provider also did not leak any information when conducting a p2p address detection test VPN, indicating that ExpressVPN is a leak-free service! Even you can explore the guide and get the free ExpressVPN acccounts with a hack.
2) NordVPN
Server Used For VPN Test: United States
Similar to ExpressVPN, I conducted tests on various different servers of NordVPN. I even reached out to a representative based in the United Kingdom to connect to one of their US servers.
This is because I myself am based in the US, so to receive accurate results I needed someone to test VPN server from a different location.
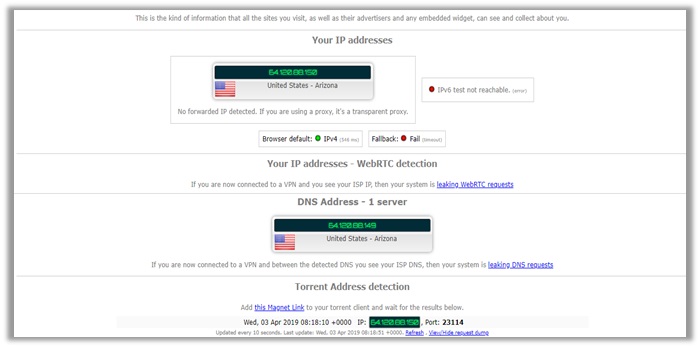
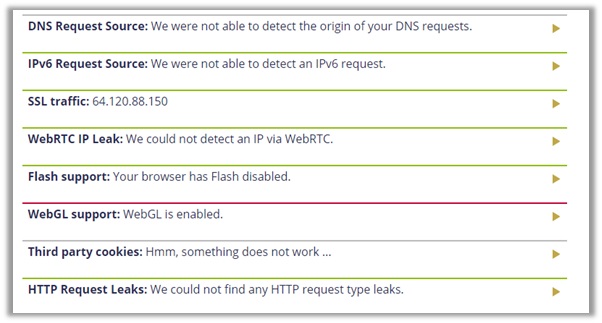
As you can see, the results show that NordVPN successfully masks your true location, cloaking your IP address, WebRTC, and DNS address.
It even passed the p2p address detection tests, using the same IPv4 address. To double-check, you can see the results from doileak.com too.
In comparison to ExpressVPN, the Panamanian-based provider did not reveal any DNS request source. This guarantees that NordVPN is a safe, log-free provider you can trust! Even you can avail the NordVPN free version for 7 and 30 days.
3) Surfshark
Server Used For VPN Test: Netherlands
Surfshark may be a relative newcomer, but the BVI-based provider continues to impress privacy-conscious users. It offers great unblocking, torrenting, and anonymity. Even it is in the list of cheap VPN services.
I conducted tests on several locations, but have showed you the results on their Netherlands server. You can see, the provider suffers with no leaks whatsoever.
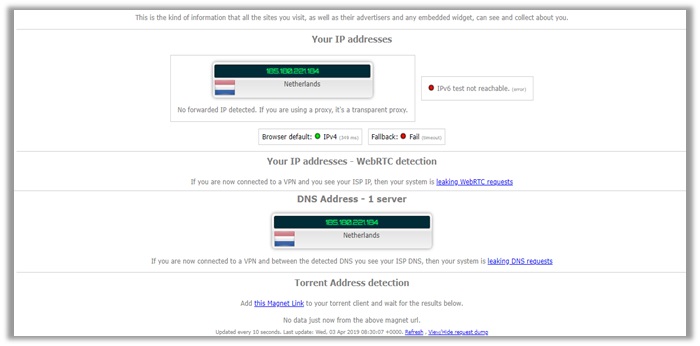
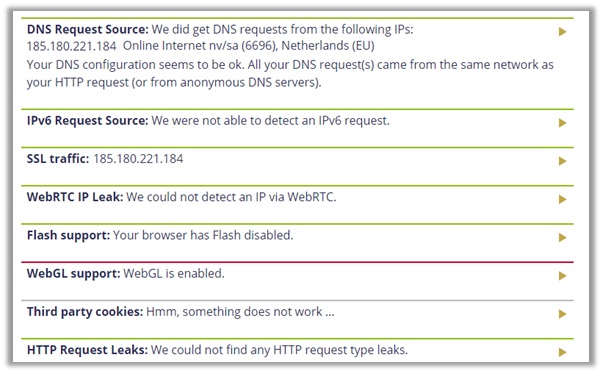
My IPv4 address is safe, WebRTC is undetectable, and DNS address also reveals the same IPv4 address – indicating Surfshark offers strong privacy.
I double-checked the results with doileak.com and other leak test websites. The performance of Surfshark remained consistent, even when conducting a torrent VPN test.
4) VyprVPN
Server Used For VPN Test: Romania
Based in Switzerland, VyprVPN is among the only few providers that have a verified no-logs claim available to the public, audited by Leviathan Security Group Incorporated.
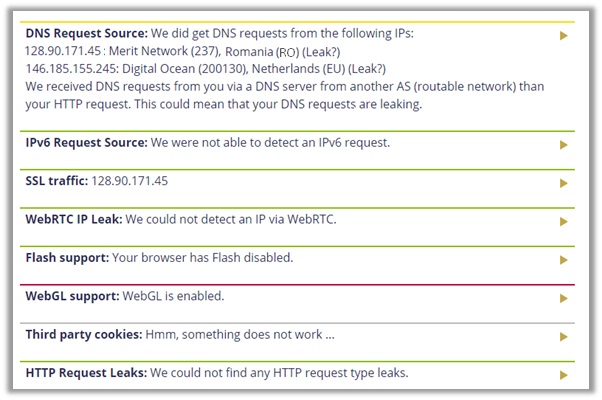
When testing their servers, the provider displayed no signs of WebRTC, IPv4, DNS, or P2P address leakages. My real US IP is hidden and secure.
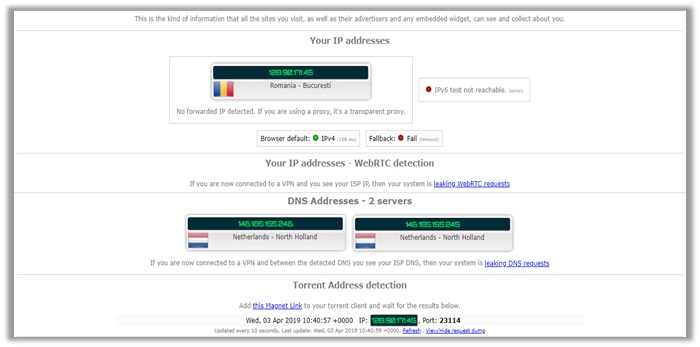
However, upon testing the provider for p2p/torrenting, VyprVPN would automatically change its DNS to a Netherlands-based address, hence why the results are mixed up below.
It shows you are connected to a DNS in Romania and Netherlands both. This still does not indicate a leak though, as our official DNS address from US was undetectable.
5) Ivacy VPN
Server Used For VPN Test: Denmark
Accredited with the Best Value and Speeds awards from BestVPN.com, Ivacy is a Singaporean-based provider that has been in the marketplace since 2007.
I tested the provider on several locations, similar to the above names. The results you see below are from my final test on their Denmark server.
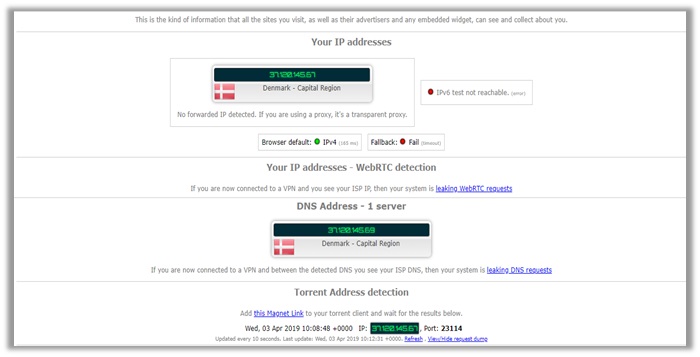
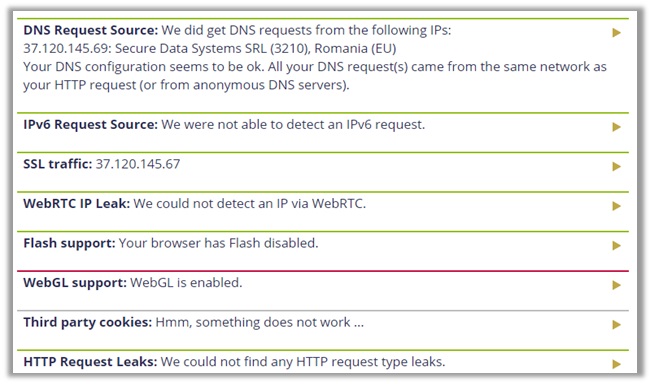
As you can see, the provider does not leak any information. Your IPv4 address, WebRTC, and DNS are all protected. Users even receive maximum security for torrenting.
The P2P address detection test was clear and used the same IPv4 address, indicating strong privacy. The results remain consistent on doileak.com too, verifying that Ivacy is log-free!
6) StrongVPN
Server Used For VPN Test: Mexico
Founded in 2005, StrongVPN exists as one of the oldest providers in the marketplace of VPNs. It is based in the US, which may put off users from trusting them.
However, I will not get that into that, as I am assessing the service on the basis of VPN leaks. For this, I conducted tests on servers to find out best vpn for Mexico For American Users in France, Australia, America.
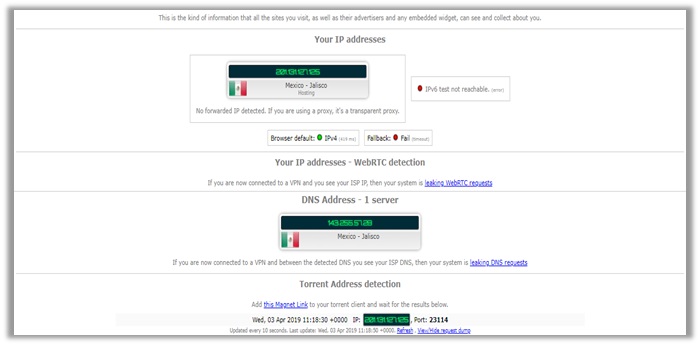
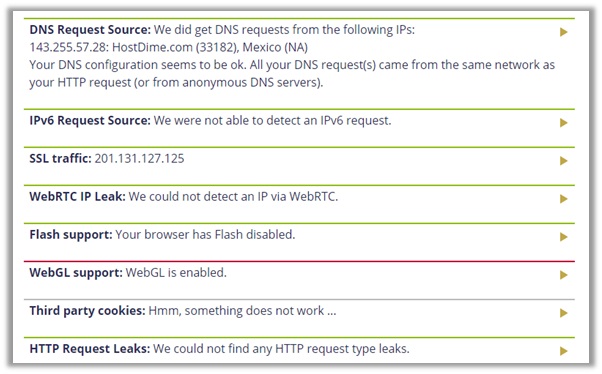
The results you see below are from my final test on their Mexico location, which is clear from any IPv4, WebRTC, and DNS Leakages. The p2p address detection tests also came out clear.
Similar to other providers, I double-checked the privacy/security offered by StrongVPN on other leak test tools, which as you can see below also came out clear!
7) IPVanish
Server Used For VPN Test: United Kingdom
The US-based provider has an abundance of endorsements and sponsorships, offering fast speeds, user-friendly apps, strong encryption, and ability to torrent anonymous.
I tested the server in numerous locations, including other Five Eyes countries like Australia, New Zealand, United States, and United Kingdom.
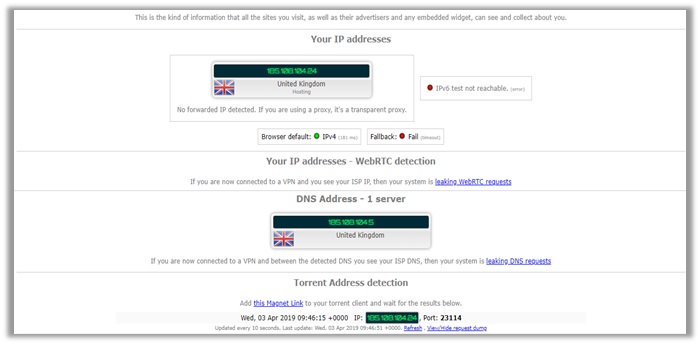
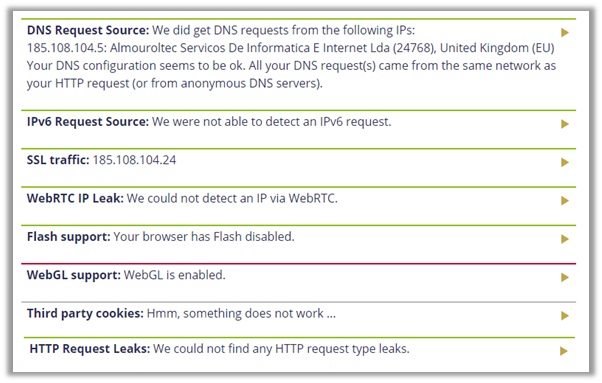
The results you see are from my final test on their UK servers. As you can see, the VPN offers solid protection, as your WebRTC, IPv4, and DNS all remain secure.
The p2p address detection test also came out clear, indicating that the provider is safe to use for keeping your identity hidden, at least in terms of strong encryption.
8) Tunnelbear
Server Used For VPN Test: Singapore
Based in Canada (Five Eyes Alliance), TunnelBear uses a freemium model. It has a free plan and paid subscriptions available at the same time, hence why its popular in the market.
From the perspective of VPN leaks only, the provider offers great anonymity online. I tested it on all Five Eyes locations and other servers too, including Singapore.
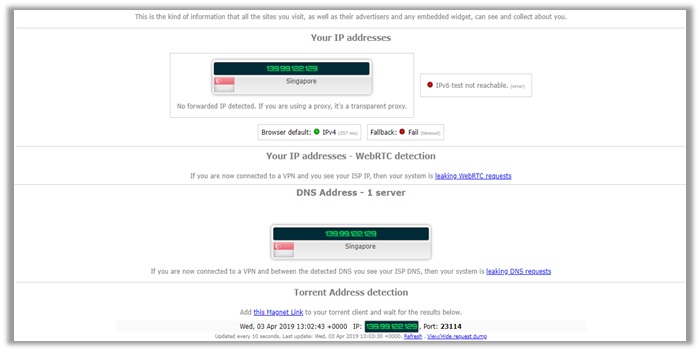
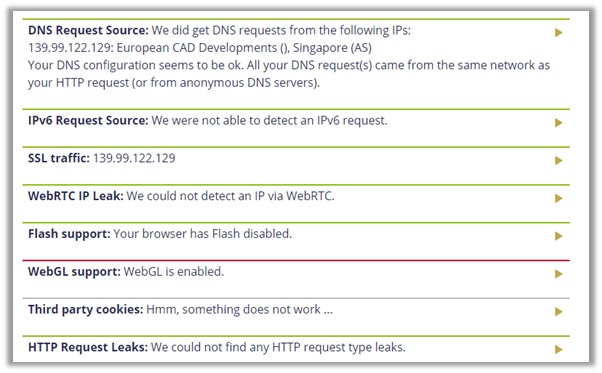
The results you see are for my final test on Singapore, which you can see are CLEAR. The provider did not suffer from any leakages of IPv4, DNS, and WebRTC.
As you can see, the VPN even cleared the p2p address detection tests, even though TunnelBear itself does not offer P2P support for torrenters.
9) Windscribe
Server Used For VPN Test: Netherlands
The Canadian-based provider, Windscribe offers a free plan and paid subscriptions, similar to TunnelBear. However, it only entered the marketplace in 2018.
Even so, Windscribe has grown immensely, despite being based in a Five Eyes Country. I will not get into details much about FVEY, but talk only from a perspective of VPN leaks.
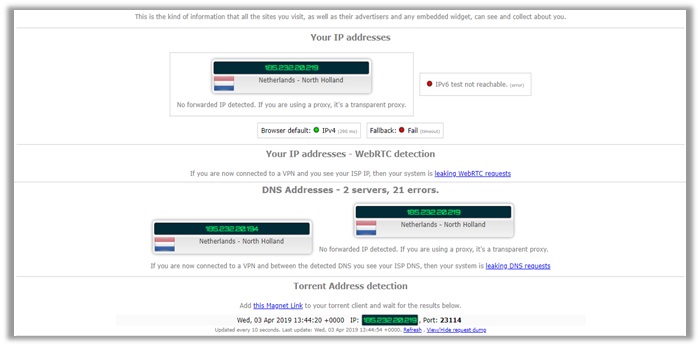
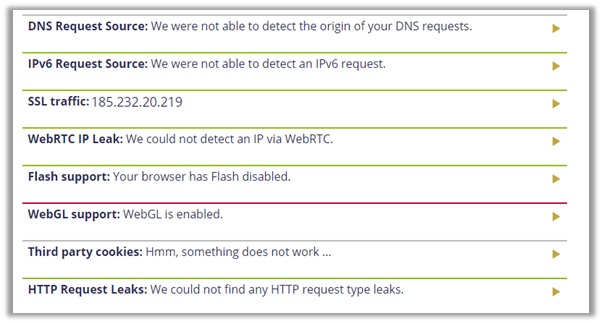
I connected to 8 different locations with Windscribe with the final one being Netherlands. The results are displayed below. The IPv4 address is secure and WebRTC too.
However, there is a problem with DNS addresses. The IPLeak.net tool encountered 21 errors assessing DNS, but it still did not reveal our true US location, so that is a good sign.
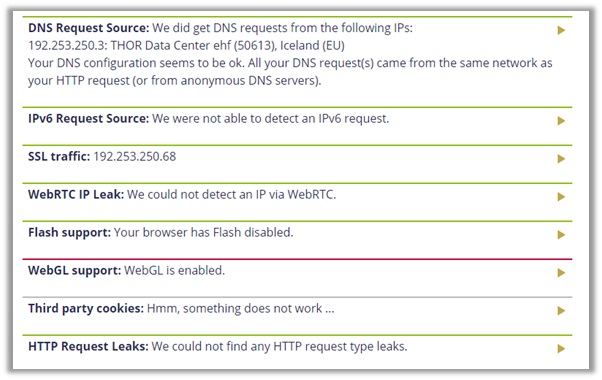
10) PureVPN
Server Used For VPN Test: New Zealand
Operated by GZ Systems and based in the British Virgin Islands, PureVPN is famous for being a budget-friendly provider.
After facing a lot of criticism, PureVPN has been working hard on improving its service. No longer do their servers leak any sort of vital information that could reveal your identity.
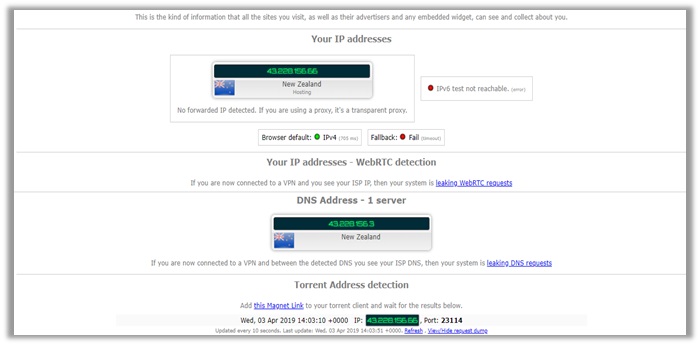
I tested the provider in 8 different locations with New Zealand being the final one. You can see the results for them below, which indicate zero IPv4, WebRTC, and DNS leakages.
The provider even passed the P2P address detection tests which signals that its incredibly well suited for Torrenting activities. But if you still want to be double sure that you are secure every time you login to the provider’s app, you can use PureVPN’s leak test tools to confirm that you are not giving away your real IP on the internet.
11) TorGuard
Server Used For VPN Test: Netherlands
TorGuard is based in US, so it may turn off potential customers, due to the location being one of the founding fathers of the Five Eyes Alliance.
However, it offers great security online and an amazing assortment of dedicated IPs, which is not very common for most VPNs in the marketplace (they usually opt for dynamic IPs).
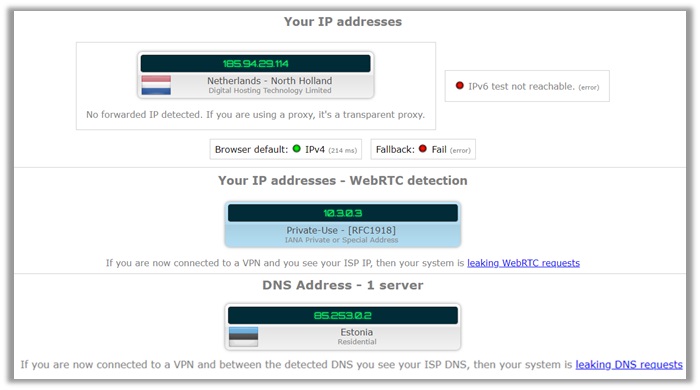
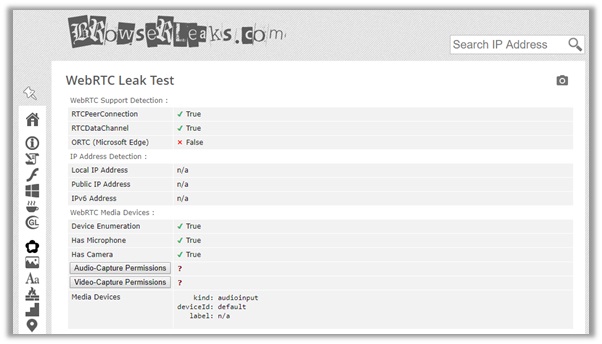
Similar to the above providers, TorGuard managed to successfully keep our identity private, after connecting to a server in the Netherlands.
As you can see from the results below, our identity and original US IP address is invisible. This means, users can feel assured to stay secure online with TorGuard.
12) Private Internet Access (PIA)
Server Used For VPN Test: Australia
PIA has proved itself as a reliable service – thanks to its no logging policies, which have been verified during an FBI case. However, does the VPN remain consistent in offering complete anonymity online?
Yes, it does! To gain an unbiased opinion about the anonymity of PIA, I decided to perform a test on IPLeak.net and doileak.com. I connected to a server in Victoria, Australia from our US location.
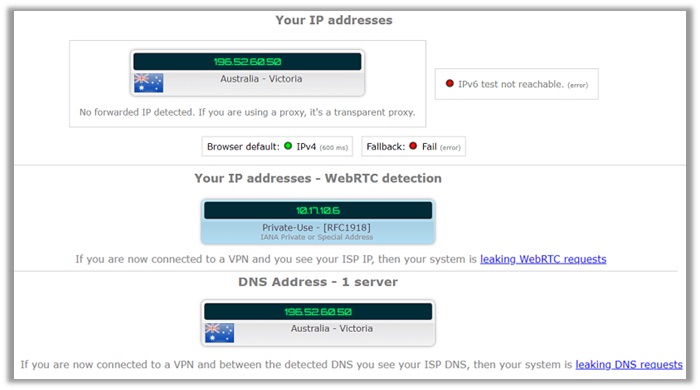
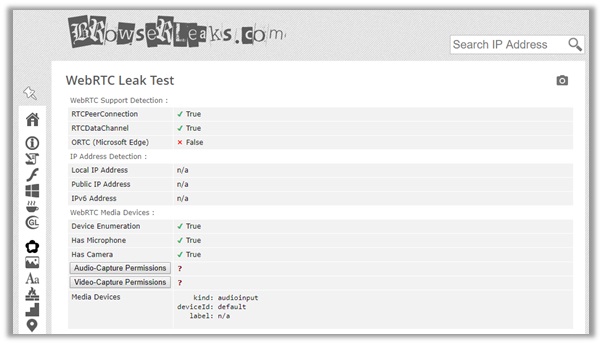
You can see the results below, which reveal zero information about our connection to an Australian server from the United States (my real location).
There was no information about our original IP address. The IPv4, WebRTC, and DNS all indicate that you are based in Australia, guaranteeing utmost level of anonymity.
13) CyberGhost
Server Used For Testing: Germany
Based in Romania, CyberGhost VPN offers great diversity to its user base. It has over 3000 servers in 60 countries worldwide and supports all mandatory features/tools for privacy.
It is still always good to get an opinion about leak issues with VPN providers. Now, you can opt to do it manually, but then why would sites like IPLeak.net come in handy.
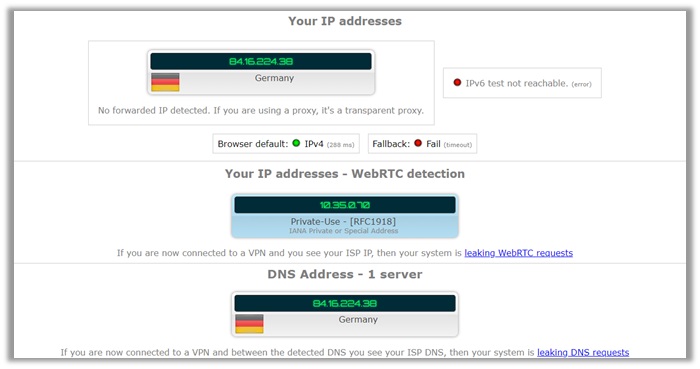
If you look at the results below, you can see – there are no signs of any leakage from any aspect. The IP address is that of a German location, including the local IP.
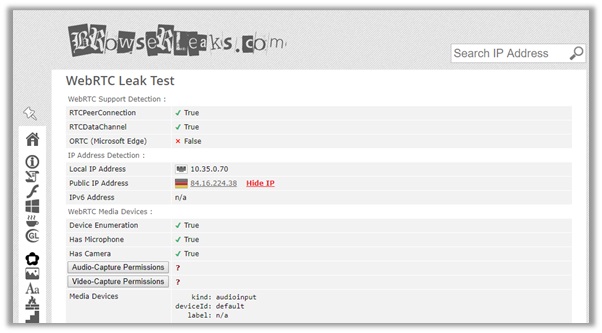
The DNS server too is the same as the cloaked IP, which means that there are no leaks whatsoever! You can check the test from browserleaks.com to verify their anonymity too.
14) IVPN
Server Used For Testing: Italy
Based in Gibraltar and established back in 2009, IVPN has been in the marketplace for quite some time, offering quite the amazing platform support, no-logging experience, and instant unblocking of Netflix.
Fortunately, there were no gaps found while testing IVPN. The default IPv4 address is of a location in Italy, and even the DNS address gives no indications to what our original location actually is.
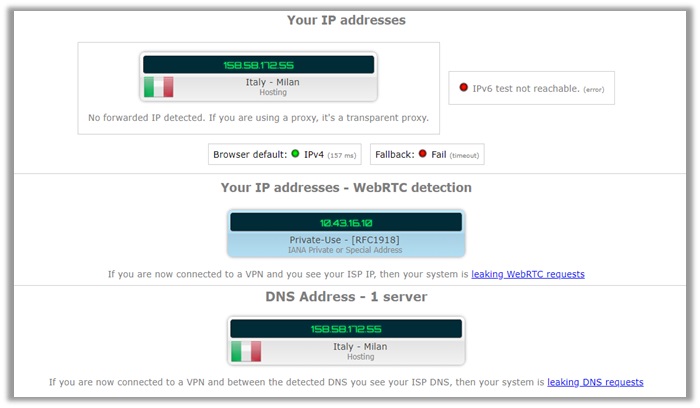
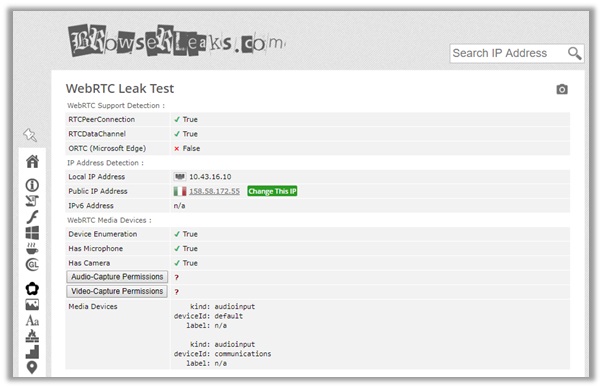
I conducted a separate WebRTC leak test from Browser Leaks by connecting to a server in Milan, Italy. If you see the results below, you will notice that only a single DNS server is visible, which is located in Italy.
This means, your identity is completely secure with IVPN, as there are no signs pointing to our official US location or DNS address. IVPN is a leak-free provider!
15) Buffered
Server Used For Testing: Denmark
Based in Gibraltar, Buffered is a relative new name in the marketplace, offering remarkable security features, huge list of servers, and responsive customer service.
The provider successfully manages to meet all expectations. The test below shows no leakage of local IP address, WebRTC, DNS or IPv4 addresses!
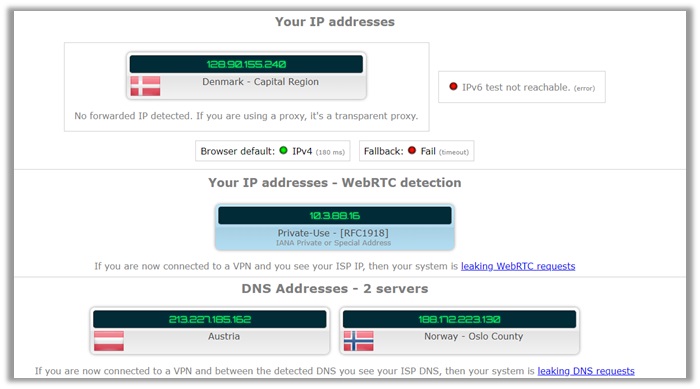
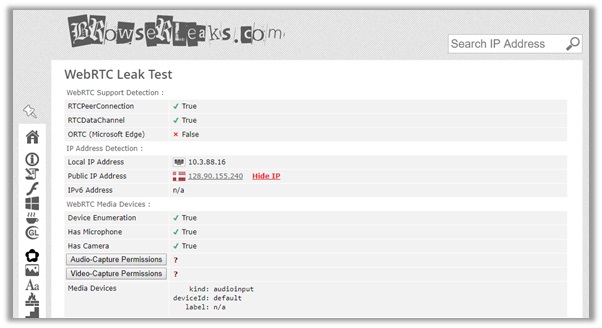
This ensures that no information leaks to cybercriminals, government agencies, and local ISPs. There are only details about an IP address from Denmark.
The DNS address also shows two locations: one from Austria and another from Norway. However, there is still no information about our local IP from within the US!
16) ZenMate
Server Used For Testing: Switzerland
ZenMate made its way into the marketplace back in 2014. Initially, the service was a FREE privacy extension for Chrome. However, later on it jumped the paid bandwagon.
To ensure ZenMate is safe to use, I performed a complete privacy analysis. From the results below, you can see our true US location is hidden.
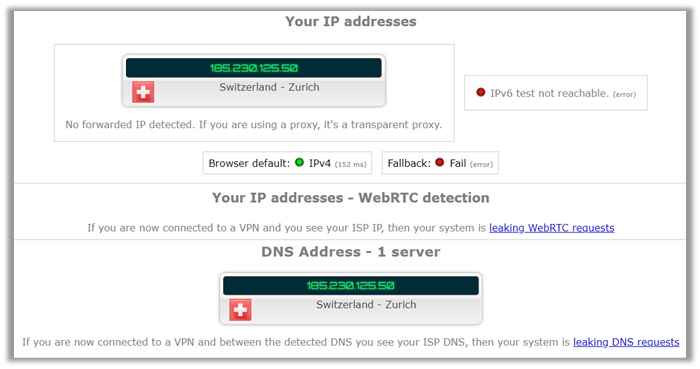
The IPv4 address indicates a Switzerland-based location, along with the DNS. The WebRTC is undetectable, meaning you are safe online.
To double-check, i conducted another test on Perfect Privacy’s DNS Leak Test tool, which also displayed the same address as in the tests from IPleak.net.
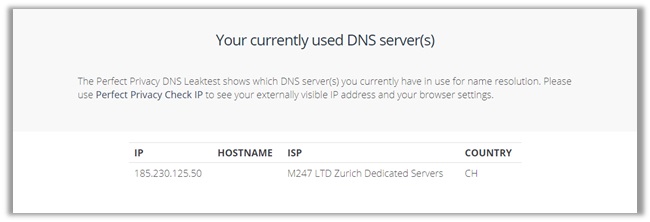
17) Mullvad
Server Used For Testing: Singapore
Based in Sweden, Mullvad is undoubtedly one of the most privacy-focused VPN services in the marketplace. The VPN offers a huge assortment of advanced features for maximum safety.
Below I conducted a complete privacy analysis from IPleak.net. The process involved connecting to a multiple servers in 8 locations, which include Five Eyes countries and Singapore too.
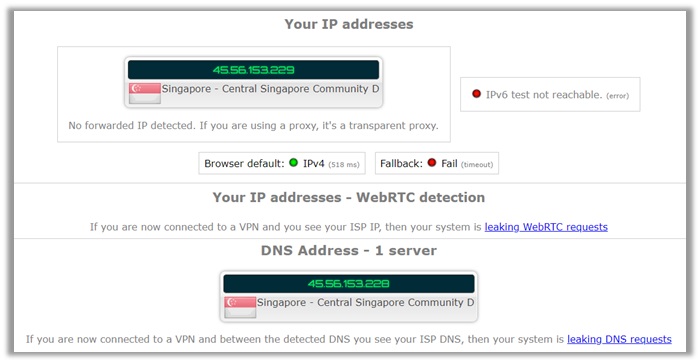
As you can see, the results below show that Mullvad successfully managed to cloak your identity, with no leakages! The IP address is that of a Singapore location, including the local IP.
The DNS server too is the same as the cloaked IP, verifying that your identity remains secure, positioning Mullvad in a trustworthy list of leak-free providers.
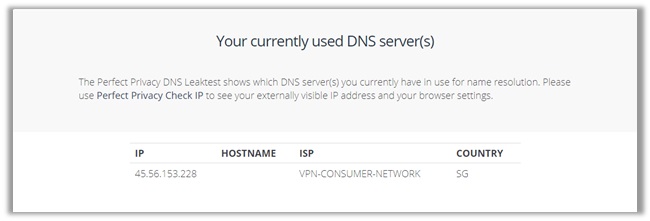
18) GooseVPN
Server Used For Testing: United States
Launched in 2016 and headquartered in Netherlands, GOOSE VPN may not be up to spec with market leaders, but is getting popular day-by-day.
It is a promising young service, offering quite the appealing features. These include unlimited simultaneous connections and its own VPN network.
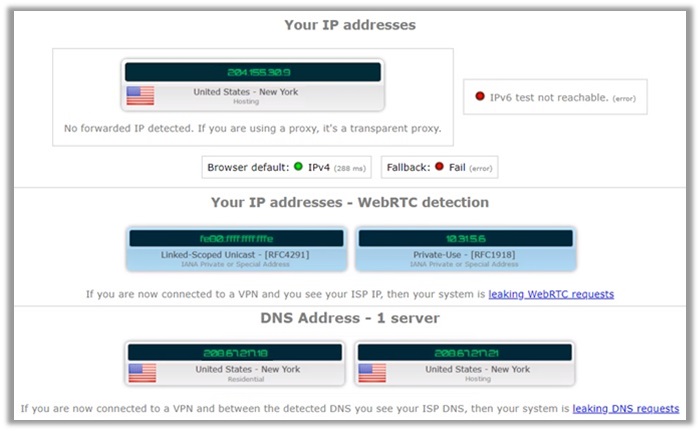
While doing my research on GOOSE VPN, I came across plenty of users complaining that the service leaks your DNS and WebRTC, especially on the US server.
However, if you see the results above, you can notice that all geolocation checks appear to be in their advertised location. A representative conducted the test from United Kingdom.
VPNs that Suffer with Leaks
Sadly, not every VPN provider is leak-free or delivers fast speeds (read this VPN Speed Test guide). It is also important to be wary of names that do leak your WebRTC, DNS, and IPv4/IPv6 addresses.
Bear in mind that leaks completely undermine the usefulness of VPNs, exposing your true locations and activities before the prying eyes of cybercriminals, secret agencies, and local ISPs.
Do not sign up with providers that have a reputation of leaking vital data. If you do, make sure to test your VPN, like I did with the above names.
For the VPNs listed below, the testing process was same. I have summarized what leaks were commonly found:
- VPN Gate – Based in Japan, VPN Gate is a free VPN service that suffers with DNS leak issues. I would not trust the provider with my digital privacy at all. Free VPN services are a fraud. If they are not leaking your IPv4 or DNS, they store logs sold to third party services for money.
- TouchVPN – Headquartered in the US (Five Eyes Country), TouchVPN is another free service. It is slow, logs your information, and does not support VoDs. The worst part, however, is the leaking of your IPv4 address – defying the entire purpose of using a VPN in the first place.
- Betternet – Located in Canada (Five Eyes Country), Betternet offers a free plan and paid subscriptions. Although their Windows, Android and other clients are safe from leaks, the Chrome Extension does leak your IP address.
- Speedify – The US-based provider already faces a lot of heat, due to its unsafe location. However, if that were not bad enough, Speedify also suffers with DNS leak issues. I would not recommend using the provider if it is privacy that you are craving.
- SecureVPN – A rare provider with no centrally located headquarters, SecureVPN boldly states that they hold the “key to online privacy”. However, this claim is FALSE, as the provider does suffer with IP and DNS leak issues, in all the tests we conducted.
- VPN ht – Based in Hong Kong, VPN.ht has gained a lot of reputation in the marketplace. It does not log any information and exists outside the surveillance eyes countries. Unfortunately, the provider leaks your IPv4 and DNS address, deeming it unworthy of protecting you online!
- Hola VPN – Headquartered in Israel (a close partner of the US Government), Hola VPN is a risky option itself that requires a lot of blind trust. If being an official “observer” to the FVEY was not enough for Israel, Hola VPN also leaks your WebRTC and DNS address, failing all of our tests.
- Hoxx VPN – Located in the US, Hoxx VPN cannot be trusted to keep your identity secure anyways, but matters get worse when you find out, they also leak your DNS, WebRTC on various clients and suffer with more leaks on their Chrome Extension.
- BTGuard – The Canadian-based provider already has to deal with a lot of heat, due to being located in a Five Eyes Alliance country. However, the VPN also failed our leak tests, giving away the real DNS address – which also led to an instant block while torrenting!
- Ra4W VPN – Another VPN service based in the US, Ra4W VPN does offer good customer service. Nothing more than that. Their client was found leaking DNS addresses and even contained malicious programs in the install file. I would not trust the provider one bit!
- DotVPN – Based in Hong Kong, DotVPN started off real good. Their location gave them a strategic advantage over others in the marketplace. Unfortunately, the encryption offered by the provider is quite weak, leaking WebRTC in our tests.
- AceVPN – Headquartered in the US, AceVPN is not only based in an “Internet Enemy” location, but is also found logging vital information data about users. To top it off, the VPN even failed on our WebRTC and DNS leak tests. I would not consider it a safe option at all.
Flawed Protocols/Bugs Linked with VPN Leaks
Online privacy and security is perpetually a game of cat and mouse. No system is free from errors. As time passes, you may also uncover numerous vulnerabilities.
Same is the case with VPN services. Providers may try protecting you by using various algorithms and combinations of encryptions, but there are bugs that could hinder your privacy like:
Heartbleed
A security bug found in the OpenSSL cryptography library (used in the TLS protocol), introduced in 2012 and disclosed publicly on April 24. It allows for the stealing of protected information by the exploiting the SSL/TLS encryption.
The bug allowed anyone on the internet to read memory of the OpenSSL software, compromising the secret keys used for encrypting traffic and identifying service providers. It also reveals the names and passwords of users.

As such, the exploit allowed attackers to spy on netizens, by impersonating providers. What it also created was a pathway for hackers to create impersonations of target OpenVPN servers that relies on the OpenSSL cryptography.
Private keys underpinning VPN connections were vulnerable to Heartbleed, with the exception of providers who were using OpenVPN with TLS authentication, as it uses a separate private key for encrypting and authentication TLS traffic.
Privilege Escalation Bug
A privilege escalation bug made the headlines 6 months ago in popular VPN clients: NordVPN and ProtonVPN. Discovered by Paul Rascagneres of Cisco Talos, the bug used a patch that prevented arbitrary code from running with admin rights.
Of course, both providers instantly released a solution for the bug. However, how it exploited the OpenVPN tunnel for gaining elevated privileges was truly remarkable, and just goes to show how clever some hackers can be, when it comes to access private DATA.
The bug typically allowed OpenVPN configuration files to contain malicious code for gaining under elevated rights in Windows. A demonstration by Rascagneres shows how the bug allowed him to open notepad.exe with the ProtonVPN service.
The bugs are currently tracked as CVE-2018-4010 for NordVPN and CVE-2018-3952 for ProtonVPN. Both providers used a separate approach for fighting the bug. Proton placed the OpenVPN in the installation directory to prevent altering, and NordVPN used an XML solution.
Tips/Settings for Preventing All Sorts of VPN Leaks
The above tips for helping counter WebRTC, DNS, and IPv4/IPv6 leaks should prove useful. However, if you are incredibly privacy-conscious, other factors need consideration.
Of course, choosing the right VPN that offers maximum anonymity is necessary, but apart from that – you can follow these tips for additional security from leakage issues:
Disable WebRTC in Your Browser
Famous browsers like Opera, Mozilla Firefox, and Google Chrome all have WebRTC enabled by default. Internet Explorer and Safari do not, hence they are not affected by leaks.
Either way, if you conduct test your VPN and you are affected, you have two options: switch to a browser that does not use WebRTC or install an extension to block the script.
- Chrome and Opera – You can install the ScriptSafe Extension from the Chrome Web Store for disabling WebRTC in your browsers. Opera users can also add this extension to their browser via the Opera Add-ons store (previously you had to indulge in a manual installation process).
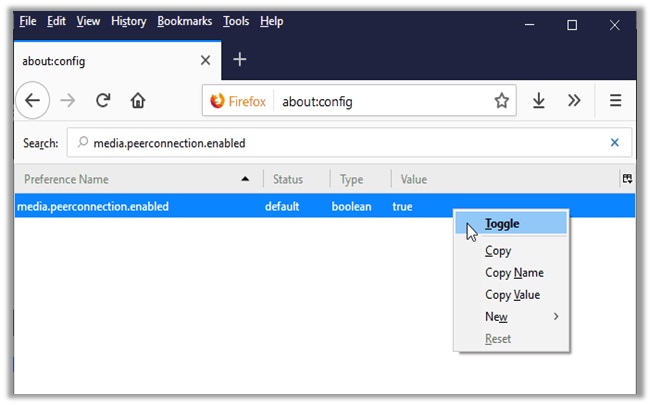
- Mozilla Firefox – You have two options for this browser. Access the configuration tab by typing ‘about:config’ and changing the “media.peerconnection.enabled” setting to false or install the Disable WebRTC and NoScript extension from the dedicated store.
Configuring a VPN on Your Home Router
This process may sound a little complicated, but I’ll try making it as easy to consume as possible. Firstly, some routers support VPN connections, and others do not.
- To figure out if your does, you will have to log into your router dashboard. You can do this by either typing 192.168.0.1 or 192.168.1.1 into the URL of your browser.
- Once done, enter your credentials. You can find them in the router manual, by consulting your ISP, or googling the default login details of your router model.
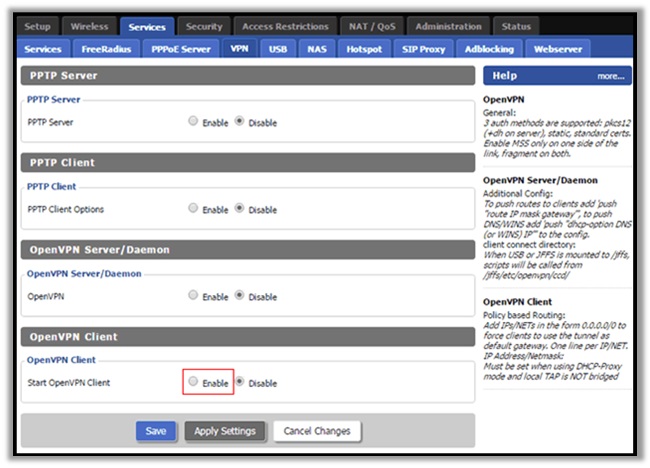
- Now in the router dashboard, look for a way to setup a VPN connection. Most routers will have a “services” tab, following a “VPN” sub-tab.
- If none exists, you will have to upgrade the firmware to an open-source counterpart, DD-WRT. Download the configuration from the router database here.
- Click on “Firmware Update” in your router dashboard, upload the configuration you downloaded, and head to the VPN sub-tab.
- Enable “Start OpenVPN Client” option and fill out the necessary details based on the VPN provider you selected to use.
Getting a Pre-Configured VPN Router
For the non-technical users, the above process may seem quite complicated for testing VPN security. Do no worry though, as I do have an alternative available for you.
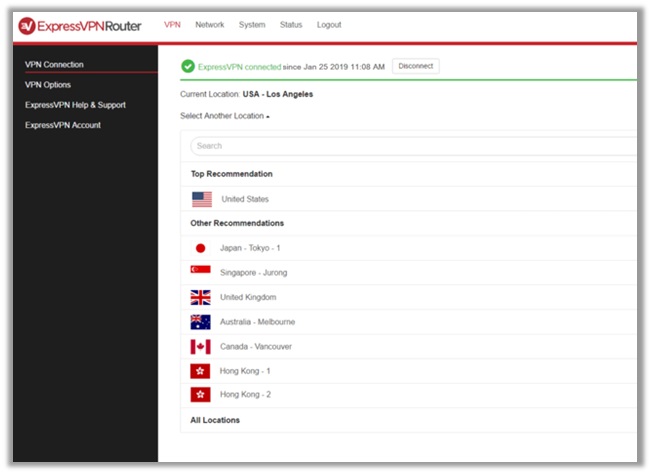
It comes in the form of buying a VPN-secured router. These devices come pre-installed with a provider-specific software, which guarantees consistent protection.
You can find pre-configured DD-WRT and Tomato VPN routers from the experts at Flash Routers. Users have choices of 16 different providers available.
I would personally recommending using ExpressVPN’s though, due to its various configuration options. Their router also comes with a built-in app called the “ExpressVPN Router App”
If you want access to this app, it comes free for users of specific Linksys router models. These include:
- WRT1900AC 13J1
- WRT1900AC 13J2
- WRT1900ACS
- WRT1200AC
Wrapping Things Up
With this, I come to an end of this VPN Leak Test Guide. I hope the information assists you in finding a suitable provider that best suits your needs and requirements.
Just remember that it is always good to conduct a leak or VPN Speed Test of any service, before signing up. A VPN may look good on the outside, but could have plenty of issues that could risk your anonymity.
Considering how countries are increasingly demanding for more control over user data, it is only wise that you be completely sure about your decision of a VPN.
If you have any questions/concerns, do not hesitate on dropping a comment below. I will personally respond and try providing as much assistance as possible.
Also, help a brother out by sharing this guide to other privacy-conscious users wanting to learn more about VPN leak issues. Have a lovely day ahead!
